The Garage Podcast : S2 EP12
Jason Masker of Upstream
We talk vehicle cybersecurity with Jason Masker, Director of Solutions Architecture for Upstream who joins host John Heinlein, Ph.D., Chief Marketing Officer of Sonatus. This discussion highlights the evolving (and challenging!) landscape of vehicle cyber threats. Jason explains what Upstream is doing about that threat, empowering OEMs with solutions and how collaboration with high quality data sources can improve the ability to detect threats quickly.
Listen to audio only version:
Episode Transcript | Jason Masker of Upstream
Table of Contents
- Overview
- Meet Jason Masker
- Upstream’s Cyber Report
- About Upstream
- OEM’s strength vs cyber threats
- Vehicle software and SDV
- Better data on threats
- Upgrades to respond to threats
- The risks of inaction
- Customer confidence hurt by hacks
- SDV’s can be safer
- Examples of recent threats
- Wireless as an attack surface
- Conclusion
Overview
JOHN: Today in The Garage, we’re recording live from Auto Tech Detroit 2024, and we talk cybersecurity with upstream. Let’s go.
JOHN: Welcome to The Garage. I’m John Heinlein, chief marketing officer from Sonatus. We’re recording live from Auto Tech Detroit 2024. And our guest today is Jason Masker.
Meet Jason Masker
JOHN: Jason is Director of Solution Architecture for North America for Upstream. Jason, welcome to The Garage.
JASON: Good to be here.
JOHN: We always like to get to know our guests at the beginning. Tell us a little bit about you and your background.
JASON: So my background is in, solution architectures and technology. So very deep background with technical solutions, data, and also cybersecurity consulting.
JOHN: Where were you before upstream as well? You had a great background.
JASON: Yeah, I spent, I spent just prior to Upstream. I was spending, about two years, pretty exclusively focused on the Fortune 1000. So about 850 accounts. We were very close to building solutions. So in that role, I was executive leadership. I also had, field CTO role, and I incubated a data intelligence team to come in and tackle some of these data projects.
JOHN: Fantastic. And where are you based out of?
JASON: I’m based out of Metro Detroit, up in Rochester Hills. So, very happy to be here. at Auto Tech.
JOHN: And we hope to be able to catch you while we’re in town.
JASON: Yeah. Yeah.
JOHN: So we always like to get to know our guests. And we always ask them to tell us a fun fact. Something interesting about them. Tell us something interesting about you.
JASON: So fun fact. My go-to is really, just because it’s probably a little unique for the technology industry is that I used to have 16 goats.
JOHN: 16 goats?!?
JASON: Outside a small RV farm, primarily milk goats. My daughter had a health issue where she needed the fresh goat’s milk, and we just, made a family, project of it.
JOHN: That’s fantastic. So many of our neighbors, like, you can have chickens. You can have, like, two chickens in San Jose. I don’t have chickens. I can’t touch your goats story, that’s an incredible story. I do love to grow, fresh tomatoes. So I have some, most years, really amazing tomato plants this year. I’m not sure how that’s going to go, but. So we can have amazing tomatoes in the summer, and there’s nothing like a fresh tomato that’s been picked five minutes ago.
JASON: Nice. Yeah. That’s great. I love Caprese salad, so…
JOHN: Yeah. That’s it.
Upstream’s Cyber Report
JOHN: So you just released- Upstream just released- a report on cybersecurity and I wonder if you can share with us some of the kind of scary conclusions you find in your analysis.
JASON: Yeah. So the cyber report, you know, we’ve been doing it since 2019. It gets a lot of, opens up a lot of discussion in the industry. We get kind of asked to do executive briefings and things on that all the time. And what’s very interesting this year is we’re socializing what we see as this inflection point.
So early on, we’re seeing a lot of research activity, as vehicles, you know, are getting more smart as, as, smart mobility is kind of coming along. people are, you know, knocking on the door interested in things. What we saw this year is that, you know, 50% of publicly reported incidents had the potential to impact many vehicles versus, a single vehicle.
So we’re talking about thousands or in some cases, even millions of vehicles, and this is this is a huge swing. so, so in the years prior, 2021, 2022, that was only 20%. So we’re looking into that, where we’re looking at, 95% of incidents are carried out remotely, with 85% having a extreme remote, we’re talking like cross-continental. We’re seeing that 64 of incidents now are by black hats. We’re seeing, we also have a, cyber threat. so we’re monitoring, like, deep and dark web activity. That activity is up 150%. Just the chatter and kind of activity around, hacking and fuzzing this, mobility space. So I guess the message is that this is accelerating and, the impact of the challenge is dramatically increasing. So we need to be matching that, right, with our activities.
JOHN: Oh, that’s incredible. So if that hasn’t scared the hell out of you, I don’t know what will. I think these cyber threats are only increasing.
About Upstream
JOHN: I think it’s a perfect opportunity for them to introduce Upstream and and talk about what you do as a company to try to help mitigate some of these threats.
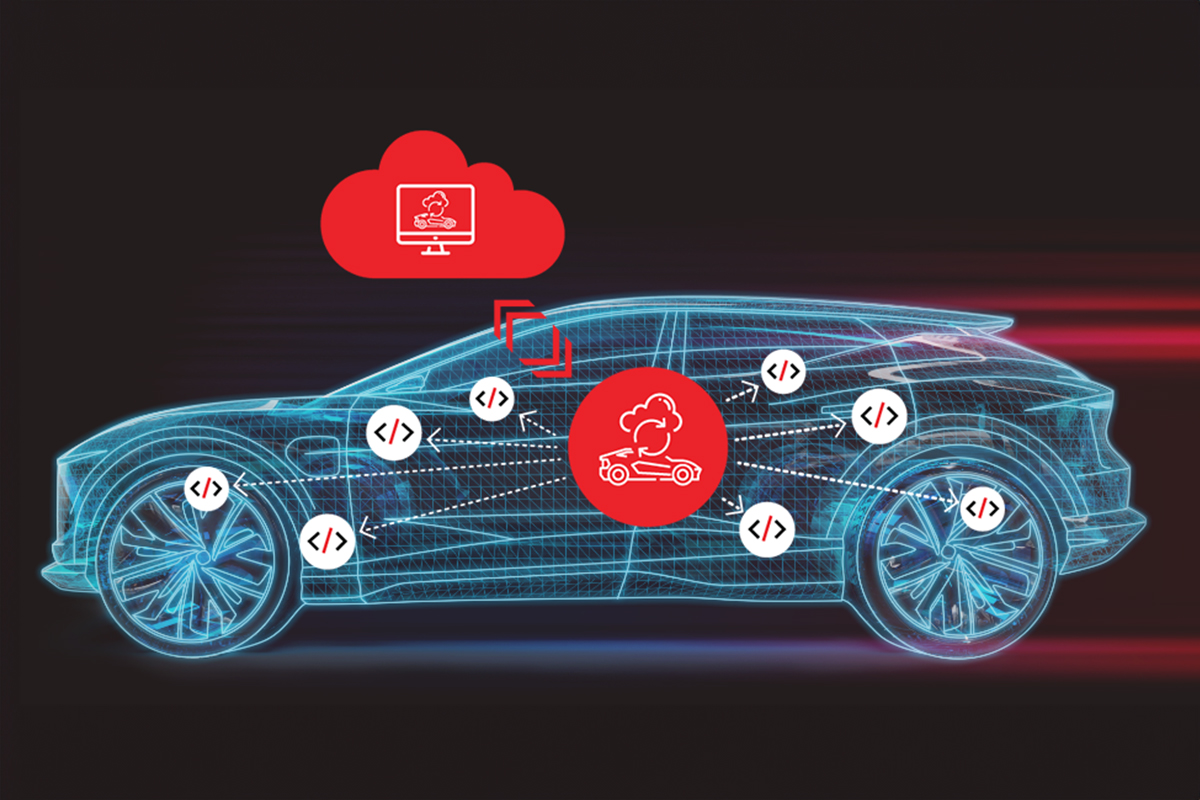
JASON: Yeah. So Upstream has been around since 2019. And we have three primary, like our go to market around product offerings. The flagship is a cybersecurity platform for mobility, where we, we’re monitoring now over 25 million connected vehicles, for our customers. And, this is to be looking real time, analyzing the telemetry the API calls on the back end and sort of everything that’s part of this ecosystem and doing the correlations.
So the only way we understand this, these events and things are related. and so that’s about what’s happening today. If I’m under attack today, I want to, I need to be alerted, I need to take action. And then and then to get ahead of it, we also have a cyber threat, intelligence product. It’s very catered, especially to mobility, where we have a lot of vendors, we have a lot of technologies we’re bringing together into one product. and this is about S-BOMs, H-BOMs, really understanding at a component level what’s involved, so that you can better monitor, you know, the CVE feeds, the vulnerability feeds and know what is the impact to you in your product. And how can we get ahead of it?
With that, we’re also monitoring threat actors. We’re monitoring the deep and dark web.To also look at things like sentiment, you know, fraud and theft and that type of thing. And, so that we can you can see the progression of, okay, now, I know, this vulnerability is impacting me, and I need to get more urgent when I know that not only is that vulnerability out there and I know it impacts, but now other people know it impacts my product, and now they’re targeting my product.
And so it adds to the urgency. But yeah, that lets us kind of get ahead and maybe prevent things before, our cyber security product is detecting an on an all-out attack.
JOHN: That’s that’s fantastic.
JASON: The other offering is really, we take this expertise in the mobility domain, and, we provide what we call VSOC or vehicle security operation center services. so we do this in a build, operate, transfer, often for larger customers that have their own SoCs. For customers with their own cyber platform, we’ll do that that as an escalation, as a level 2 or 3. Or we can do it completely as a managed service, where that’s needed to bring really that mobility domain expertise is not the typical IT SoC skill sets. It’s a little different, right. So, to try to round that up and help with the playbooks, to be effective as an organization.
JOHN: That’s fantastic, because I think in so many of these areas that we talk about a carmakers, automakers are needing to bring in disciplines like in this case, cybersecurity that may be not native to them, but maybe they may have some operational expertise that’s close to their fleets, for example. But when it comes to these threats, it’s probably not their skill set. So bringing in partners like you can be helpful.
JASON: Yeah, a lot of times we’re helping with those motions. You know, how do we bring product and cyber closer together and make it more of a working relationship. Right. because at the end of the day, it’s it’s, we’re developing a capability, an organizational capability so similar to an organizational capability change, a great deal for the auto space, right? When we started to build the smart cars in that we need this new capability of, the higher tech things, with the vehicles. We also need a capability an a proficiency of doing that securely, right?
OEM’s strength vs cyber threats
JOHN: What’s your perspective on the OEM landscape? I don’t want to name names here, but just generally speaking, are you feeling like OEMs kind of get it? They get these threats? And how how uniformly do you see them rallying to make the kind of needed improvements such as your products?
JASON: So it’s interesting. We’ve actually, we’ve actually tried to break that down. We talked to a lot of, obviously we talked to all the largest, autos. We have, also very small ones or startup, auto manufacturers, right? And we looked at this from, you know, you can look at it as organization size, in terms of people, in terms of money.
You can look at it at as fleet size, in terms of how many vehicles do they actually have on the road. And what’s interesting is there’s not really one of those that predicts their security, proficiency, because we find them all different sizes and all different postures. And if you think about it from that, you know, we’re developing ultimately a capability where, you know, we’re certainly happily to bring the tooling to help with that.
But we’re also developing, you know, an organizational efficiency at doing it, right? How are we shifting left in these APIs and things that we’re developing? And we want to do that in a secure fashion. To do that, you need a great relationship between cyber and saying, “hey, we missed some things. We need to get this into the cycles” right?
And in order to accomplish that. So it just it takes time. I wouldn’t be discouraged. You just have to start. And it’s something that gets better with time, just like we did with the, the technology itself, with the smart cars.
JOHN: So it sounds like you’re saying there’s a, there’s a spectrum from some that are really leaning into this and others that are still ramping up, I guess.
JASON: Yeah, it gets driven from different…. So as an example, overseas, we saw in the past couple of years a lot of this driven by compliance, you know, the UN and ISO and these the EU have, you know, you need to be compliant with these, these security requirements. Domestically in the US, we don’t we don’t have that so much driven by compliance, but there’s an awareness of it and awareness that it may be coming. But some of them are driven more by more incident driven more, you know, we’re we, we put this great API out there, this great capability with an app, and now we’re, we’re having some troubles with it because people are misusing it. So it gets driven from different areas. There’s different things that bring the awareness. I think what we see ultimately, though, is once the awareness is there, it starts and it grows and it it gets better with time.
Vehicle software and SDV
JOHN: Maybe that’s a good opportunity to talk about software. You know, so much of the show here at Auto Tech Detroit. And of course, the focus of both this podcast and Sonatus in general is vehicle software. And bringing accelerating the shift to software defined vehicles. I think, and I’d love to hear your perspective, that the opportunity to deploy software to find vehicles is a real chance to put in place some of the important software you need to help address some of these issues. What’s your take on SDV’s and this issue?
JASON: So SDV’s such a large impact not only, you know financially in that when you look at things like an OTA update versus a full recall where you’re recalling back vehicles and make those change right? It also has, a major security posture impact. If you can make these…we rely…we’re only as good as the data we can observe.
We don’t produce data, we analyze data and events. Right? So we see the sophistication increasing with select telemetry. And then it’s a balance with the cost of that telemetry, right? So SDV, obviously if you can make those, those fine tune, those adjustments on the fly, even better. So you know, as we’ve been talking about where, where you have, you know, something like a Sonatus capability in the vehicle and Upstream capability in the analytics in the cloud. If we can build synergy between those, right, and really get them to work together in that respect. Because at the end of the day, some things are best done and observed in vehicle. Other things are best done and observed in the cloud, and you end up-leveling both of those at the same time.
Better data on threats
JOHN: So it sounds like… I’ll take two parts out of that. One part is there’s a real opportunity for SDV, but it’s it’s multiple aspects. One is if we can produce better data from the beginning, then you can find the needles in the haystack or find the threats quicker by having better or better data and better visibility across the vehicle.
JASON: Yeah, absolutely. And that’s a process because, ultimately, you know, we’re of course automating things that we see all the time. So we’re not so worried about those as much. But then you see something new and then you go, wow, if we would have had this metric, it would have been an earlier predictor. And now you can make those adjustments on the fly and it’s a better synergy.
Upgrades to respond to threats
JOHN: Yeah, so then the second part of that coin is in an SDV also because of the benefit of upgradability, which people often think about as you’re providing better driver features or whatever, but that also extends into cyber as well, that if you have a threat or, you know, zero day threat or something that happens right away, historically you would have had to wait a long time or take the vehicle to a service center to re-flash. Now we have the opportunity to potentially respond much faster, even preventatively, potentially, to mitigate these threats.
JASON: Absolutely. And I think where we see this going, right, is we’ve already done a fairly good job at the automation side. You know, you have, a user that’s misusing APIs. And, and we can build an automation right in the automotive cloud to go ahead and okay, let’s block those credentials. Let’s kind of kick that back.
We have less that we can do natively from the cloud for the vehicle itself, for physical attacks, for maybe there’s a Bluetooth or a Wi-Fi attack happening. Right. So in those cases, you know, I think the capabilities being developed in SDV are very nimble and there’s potential to do the same types of things we’ve been able to do in the cloud now on vehicle where okay, somebody has Wi-Fi, let’s let’s stop scanning SSIDs, for a bit, right. So this is great to have this capability upleveling in both places. I think it really builds a robust solution.
The risks of inaction
JOHN: That’s fantastic. I, you know, I wonder what are the risks here? What are the risks of noncompliance if, if, if you’re not doing this right, what’s the downside?
JASON: Yeah. So the I mean, that’s the thing in oversees. right? Compliance is a direct financial. It’s very much easier to measure. Security, we’ve always have this, ambiguity, right? It’s a bit like insurance: you know, maybe you go out, you get the cheapest insurance, and then you have an incident, and now you oh, you doubled down. You have, like, the most expensive. And then you probably if you’re really unlucky, you don’t have that type of incident again, and you’re just wasting them. So we have the same type of thing to help with that. The analytics ultimately it’s correlation. So we do work with organizations to take some of this effort and also derive more measurable impact from that. So vehicle quality prediction, if we can if we, most of our, OEM customers tell us, you know, if a recall is going to happen, the earlier we can know it’s just a major, major financial impact. So being able to help with things like that so that you can justify more of the investment with these real, tangible things as well.
Right? So we look for, for other ways to, to kind of help with that. But obviously, you know, things like the inflection point when you see that this is…you know, you have to say, well, what is the reputation impact of this ahead, you know. you definitely have to think about, your customers…
Customer confidence hurt by hacks
JOHN: Customer confidence, really, because, I mean, there were a number of, famous threats in the past few years where I’m not going to name names, but various different vehicles were hacked. And I think it causes consumers pause a little bit to think “well, maybe is that a safe vehicle for me?” And I think there’s a point at which it could impact buying behavior.
JASON: Yeah. I’ve actually actually, on the side, you know, individuals, have different reactions to becoming aware of these things and definitely have said, “Can I get a car with just like a transistor radio, you know, I don’t need it to be smart. I’m being tracked and I’m being, you know, maybe somebody is going to drive me off there?” You know, there’s a fear that that kind of comes out. We’ve got the media and entertainment also, you know, kind of amplifies this thing we see, like, Netflix, in some creative scenarios.
SDV’s can be safer
JOHN: And they’re dramatizing the downside. It’s not like that. It’s not like you see in the movies, but think it is it is interesting because I don’t think, you know, the average person is not going to go back to an old, old style radio. But rather if we… you know, I had a guest on the podcast earlier this week who was saying, ironically, software defined vehicles…You say, “Oh my God, it’s so scary. There’s so much software. It’s such a threat!”. To say, no, there’s software in the vehicle already. And it’s not protected. So actually the software defined vehicles can be the safer ones because we can actually find the threats quicker. We can then potentially mitigate the threats. So I’m hoping we can change the perspective on this to people’s thinking that it’s, it’s the right direction, not the wrong direction.
JASON: Absolutely. It’s a process and it’s a maturity. And it’s nothing that we haven’t seen across other technology or areas. Right. where there was a time when ordering something online was very scary, right? And, and I think, I think we’re all pretty comfortable with that. So it takes time. It takes some discipline and attention. But we’re, you know, we’re all here to help, and, and I think, this capability gets better with time.
Examples of recent threats
JOHN: So because you’re really behind the scenes and seeing how these threats evolve, I wonder if you could share with us some of the examples you’ve seen of some of the threats you guys have found.
JASON: Yeah. So those are always interesting. Right? So, some of these come up and it’s, it’s obviously very interesting when there, there hasn’t been this kind of perspective or insight, to the correlations before. But we’ve definitely seen and been able to stop… Obviously the researchers you know we can we see that. And it’s like “Hi, Sam Curry.” You know there he is again. And we can detect that. But we have said somewhere, we’re preventing these types of, attacks to get control of, of multiple vehicles. And we recently had, with our threat intelligence, an OEM ask us, you know, can you figure out how they’re… we really have no idea how they’re offering this on the dark web. Like, you know, how they’re saying “I can sell you full access to the infotainment” and all this stuff, like, how are they doing it? And when we engaged and and sort of observed, while we were engaging and, and doing this, to a vehicle— at their request, again, we’re not, we’re not, we’re not hacking them, for fun—we we observed, you know, that this was actually coming from the inside, that somebody on the inside is, you know, making some money on the side there. They’re a diagnostic token they can generate, with the system, and, you see it happen, and then you see that exact token get shared, and that’s incredible.
JOHN: So you’re you’re kind of, engaging the threat, almost like, engaging the, you know, and saying, hey, how is this happening? And watch, watch the process transpire.
JASON: Yeah. Live. So sometimes that’s you’ve got to investigate. That’s the way you’ve got to do it. So, there’s been there’s been other examples of attacks where we, we’ve, we actually were able to identify, that some that somebody was able to do an injection, because they found out the the vehicle was constantly scanning SSIDs, so they were able to accomplish an injection attack with an idea that was, just by setting the SSID to something that was an injection. Right. but we were able to see that based on, based on telemetry sent up from the vehicle.
Wireless as an attack surface
JOHN: Very interesting. So these wireless connections, while they bring huge benefits, also can be a source of risk.
JASON: Yeah, absolutely. And even I guess what’s even scarier about that is that there can be a large gap in the time it’s happening until, you know, it’s happening. So because we’re watching this telemetry and we’re correlating things that look suspicious, you know kind of right away, but who knows how far and why that kind of thing could spread before, before you’re aware.
JOHN: That’s that’s one of the reasons we care so much. And one of our, you know, claims to fame is really fine grained, data visibility into vehicles. And we’re able to, probe things that are much deeper than have been previously possible. And we can also adapt the data analysis very quickly because you might ask a question, a proverbial data question of a vehicle and realize, actually, I need to ask another question. Well if that time constant to change that question is very long, that’s problematic. But we can change that, that that question in, you know, in minutes or hours that can give a really fast cycle of learning when these threats are rapidly developing.
JASON: That’s absolutely. And not to kind of pound in the inflection point but but that’s exactly you know…the time is more critical now. right. So I think that, you know, being able to uplevel this is, is just super critical, to being in a good posture for, for all of it.
Conclusion
JOHN: Well, Jason, aside from the fact that you’ve scared the hell out of us, I’ve otherwise really enjoyed the conversation. And I’m really grateful for you coming to visit with us, here at the show. Thanks so much.
JASON: Yeah, absolutely. Glad we could connect. And, do this. And, it’s been a great conversation.
JOHN: If you’re liking what you’re seeing on The Garage, please like and subscribe to the episode to hear more from Auto Tech Detroit and from our season back at our home garage. We look forward to seeing you again in another episode of The Garage very soon.
Recent episodes

The Garage Podcast
Steve Bell of Wards Intelligence

The Garage Podcast
Dr. Oliver Rumpf-Steppat of BMW

The Garage Podcast
Art Hyde, Mr. Mustang
Related resources

Dynamic Cybersecurity for Connected Vehicles
Why do software-defined vehicles provide a superior platform to prevent, detect, and counter cyberattacks?
Modern Networks are the Backbone of SDVs
The rise of Software-Defined Vehicles (SDVs) promises a new era in automotive technology, where vehicles continuously improve and new features…